Modern society is far more repressive than anyone acknowledges, aided by technological surveillance of almost everyone on Earth. By surveiling, censoring, and persecuting wrongthink, totalitarians can criminalize their political opponents and control the populace.
The purpose of surveillance is control: by watching everything (and implicitly punishing anything) you do, they can control you. The fundamental ideology they push to exercise this control is tabula rasa, or the blank slate theory which states that people are essentially malleable through social conditioning. The useful idiots who are low-level enforcers often come from the political left, but also from the right (nationalists, religious fanatics, etc.).
I have recommendations on how to counter surveillance, but I do not follow my own recommendations, and it is potentially inadvisable to do so because being the only untraceable person in a room full of normies makes one a target.
Modems and routers
Modems are practically a black box, and you can basically be guaranteed to be connecting to an adversarial entity, however there is no alternative.
Proprietary router operating systems can easily execute a Man-In-The-Middle attack by sending any insecure traffic to a third party.
Recommendation: use open-source router software like OpenWRT.
Social media, big tech platforms
The bigger the platform is, the more incentive there is to abuse their audience.
- Any and all interactions are recorded, analyzed, and weaponized. Messages that you type and don't send, things you view, things you search for, how long you spend on any particular thing, etc.
- This data will be repackaged and sold to data brokers and government agencies. Your patterns of interaction will be fingerprinted and used to identify you elsewhere.
- Any content you post legally belongs to the platform, you lose your intellectual rights.
Recommendation: avoid like the plague.
Banking
- KYC is a violation of privacy, any and all financial information collected by banks can and will be used to identify you and create pattern-of-life analysis.
- By parking your money in a bank, you are enabling the rich to leverage your money via fractional-reserve banking.
Recommendation: use physical cash, barter, or Monero (to a lesser extent, Bitcoin). Hold physical gold if you can.
Programs (or as normies say, apps)
- Any program may be doing things that you may not expect, such as reading files from disk, scanning memory, seeing what other programs are running or installed, or any other form of snooping. This can be detected by tracing system calls, but most people aren't going to do this.
- Do not run untrusted programs or programs of unknown provenance, particularly pirated software carries risks of malware.
Recommendation: only use open-source software.
Personal computers
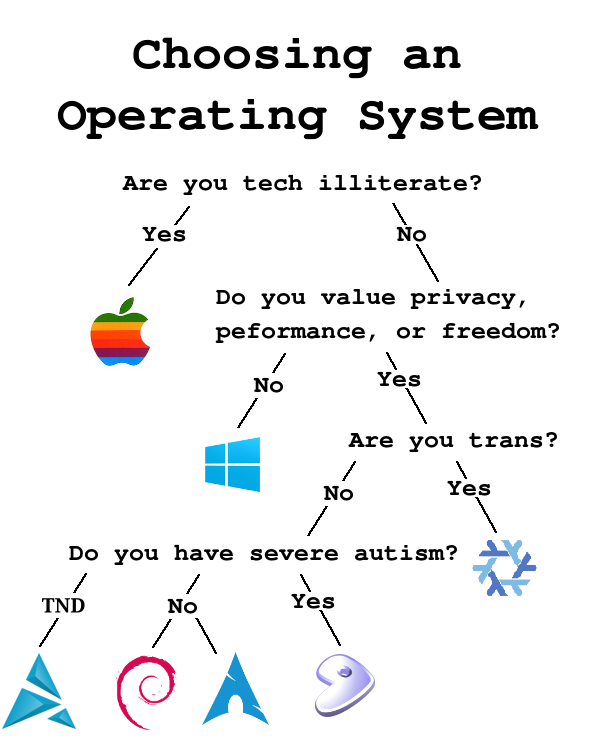
Unfortunately, most PCs are compromised at a hardware level with things like TPM, IME, and AMD PSP. The tech which purports to secure the system, is also the greatest vulnerability.
Security through obscurity, which is often derided, can be a valid defense: by using an operating system that nobody uses, on architecture that nobody uses, there would be little incentive to expend resources into backdooring some nerd autist.
- Using any closed source proprietary OS like Windows or MacOS is a guaranteed way to get backdoored.
- State-level actors like TAO can and will use undisclosed zero-day exploits, even on Linux.
Recommendation: use an outdated or uncommon architecture (PPC, MIPS, RISC-V), an obscure operating system (OpenBSD, Inferno, TempleOS), on airgapped hardware. This is obviously highly impractical.
Smartphones: glowniggers in your pocket
Smartphones are compromised in every way you can think of, and fundamentally insecure. There is every incentive to invade your privacy by all parties involved, so it is safer to assume that legal boundaries will not be respected.
- Baseband processors are independent of the rest of the device, controlling all radio communications, and can and will snoop on all traffic.
- Mobile operating systems are compromised, they can and will turn on your microphone without your consent or knowledge, and leak all of your notifications, so it does not matter if you use encrypted messaging because the client can not be trusted.
- Cell signal can be hijacked by adversarial cell towers, if you are anywhere near a protest or a crime scene, this can and will be used against you.
Recommendation: avoid like the plague.
Internet access
- Onion-routing networks like Tor are slow and most of the nodes are operated by government agencies to do traffic analysis. Operators of private nodes are often held in contempt.
- VPNs can be shady and operate entirely on trust. A bad actor can funnel all of your traffic straight to glowniggers.
Recommendation: use I2P or Tor if you have to, or a VPN that you can trust.
Physical surveillance
- Automated license plate readers can track where you drive and when.
- Facial recognition systems can identify you in public, even more advanced systems can analyze and identify your gait.
- Infrared cameras can be used outside your residence to track your activities.
Recommendation: avoid living anywhere that is urbanized, wear a mask if you can.